In 2008, the Office of the U.S. Secretary of Defense asked the National Security Agency (NSA) for help in prioritizing the myriad controls available for cybersecurity. The move came at a time when the theme “offense must inform defense” had become a White House mantra for cybersecurity.
The request went to the NSA because that agency best understood how cyber attacks worked and which ones were most frequent, and therefore was in a position to prioritize the controls. Since the early 2000s, the NSA had been refining a list of security controls that were effective in stopping known attacks based on earlier requests from the military, reinforced by guidance from the White House. The CIA’s Tom Donahue, who was assigned to the White House cyber policy team, described that guidance as “first fix the known bads.” That meant no control should be made a priority unless it could be shown to stop or mitigate a known attack – guidance that would eventually come to separate the resulting Critical Controls prepared by the Center for Internet Security (CIS) from most other lists of controls.
The NSA’s list of key controls to block the most frequent attacks was “for official use only” and could not be widely shared. However, the NSA had been participating in a public-private partnership involving the CIS and the SANS Institute for more than a decade. So when approached by Alan Paller of SANS and John Gilligan, former Chief Information Officer for the U.S. Department of Energy and the Air Force, the NSA agreed to participate in a consortium to share its attack information in order to provide its control-prioritization knowledge to civilian government agencies and critical infrastructure entities. The NSA reasoned that the military could not protect the nation if the critical communications, power, and financial sectors were not also protected.
Under Gilligan’s leadership, the resulting consortium expanded to include other groups that had access to high-value threat information, including those with large teams performing the deep after-attack analysis that disclosed attackers’ tactics and techniques. Additions included the UK’s CESG and CPNI, the FBI’s IC-JTF, and a number of companies in the incident response field that performed high-value analysis of major attacks, such as Mandiant and CounterHack. Further expansion brought in the Defense Cyber Crime Center, the Sandia and Los Alamos Nuclear Energy Laboratories, and companies like McAfee and Lockheed that had experience with major breaches.
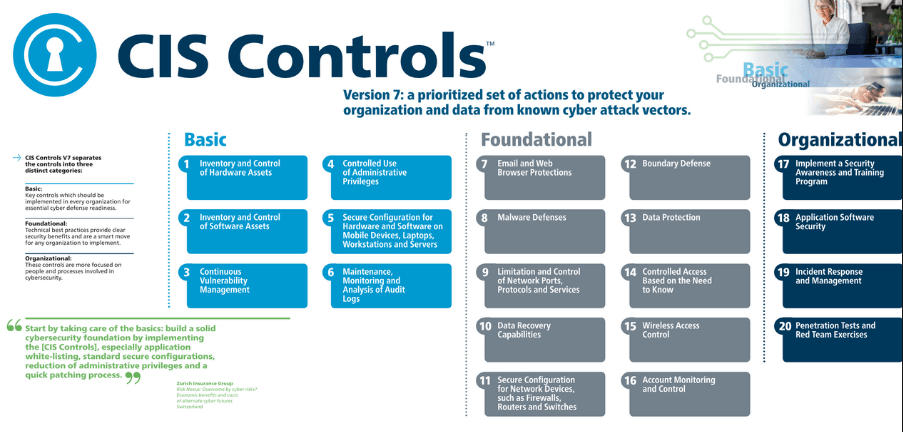
The participants built consensus at each step, surprising many by their willingness to share sensitive attack data. The clear consensus of the consortium was that only 20 controls deemed as “critical” addressed the most prevalent attacks found in government and industry. This then became the focus for an initial draft document of the CIS Critical Controls (at the time called the Consensus Security Audit Guidelines). The document was circulated in early 2009 to several hundred IT and security organizations for further review and comment. More than 50 organizations commented on the draft. They overwhelmingly endorsed the concept of a focused set of controls as well as the 20 controls selected, and they provided valuable fine-tuning to the control descriptions.
Adding even more gravitas, the Critical Controls were published by the Center for Strategic and International Studies, which, at the request of two leading members of Congress, had convened a bipartisan panel in 2008 known as the Commission on Cybersecurity for the 44th Presidency. Then, in 2009, the U.S. Department of State validated the process further by reporting that the Critical Controls aligned remarkably with the 3,085 actual attacks the department had experienced that year. The State Department CISO launched a program to implement automated capabilities to enforce the key controls and provide daily mitigation status information to State Department system administrators across the world. The program led to an 88 percent reduction in vulnerability-based risk across 85,000 systems.
During subsequent years, the consortium reconnected with members annually to ensure that the Critical Controls fully reflected new attack information as well as new techniques to mitigate old attacks. Other improvements to the controls over time have included measures to ensure that organizations know how well they have implemented the controls, as well as a list of automated tools validated through reference checks as effective in implementing the controls.
The impact of the Critical Controls has been far-reaching in both the public and private sectors. In December 2011, the U.S. Department of Homeland Security named the same CISO who had led State Department implementation of the controls to be director of the National Cybersecurity Division and Federal Network Resilience, with a mandate to reduce cyber risk across the government. At the same time, the United Kingdom’s Centre for the Protection of National Infrastructure (CPNI) announced that UK government agencies and critical industries would adopt the Critical Controls as the framework to secure critical infrastructure going forward. In May 2012, after the NSA spent a year vetting the Critical Controls to ensure that they reflected the actual risks faced by industrial and government systems, the NSA director endorsed adoption of the controls as a solid foundation for effective cybersecurity. He also cited development of the controls as an excellent example of how public and private sector organizations can voluntarily come together to improve security.
In June 2012, the Idaho National Laboratory, home of the U.S. Department of Energy’s National SCADA Test Bed, completed an analysis showing how the Critical Controls can be used in the electricity sector, a first step towards assessing their applicability to specific industrial sectors.
Since then, thousands of organizations have downloaded the CIS Critical Controls and used them to prioritize their cyber protection investments. The controls are available at www.cisecurity.org/controls/.